1 Overview
Microsoft has made OAuth authentication with Dataverse the preferred security method. This article outlines the steps required to setup OAuth authentication and configure the DynamicPoint Portal application to leverage this authentication method.
Authentication to Dataverse through Azure AD requires an app registration in Azure AD, registration of the client ID of that app in Dataverse itself and registration of that app in DynamicPoint Portal.
2 App Registration in Azure
- Logon to you Azure Portal
- Search for “App Registrations”
- Select New Registration
- Give the registration a logical name, such as “Dataverse Access Permission”
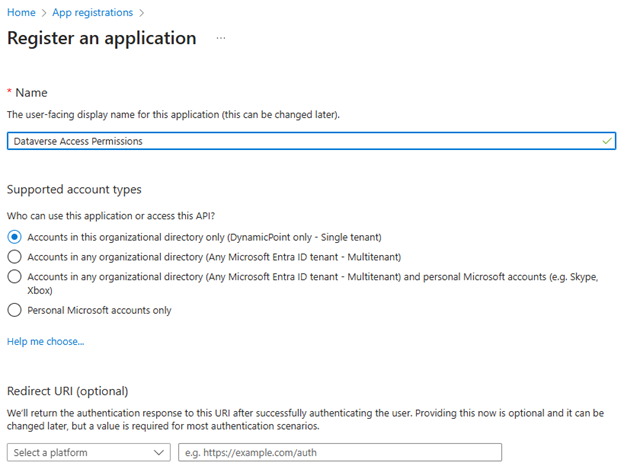
- Leave all other options as default and click Register.
- Click API permission from the left hand navigation and Add a permission.
- Under the Microsoft APIs tab select My API permissions
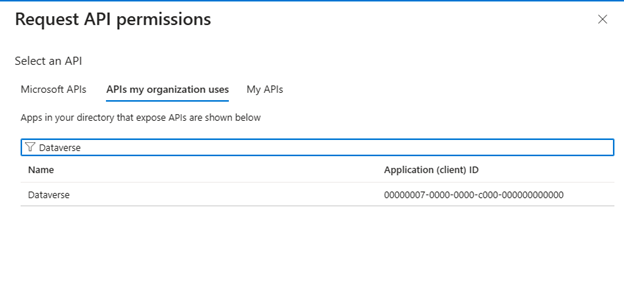
- Select Application Permissions and Click Add permission
- Check user_impersonation
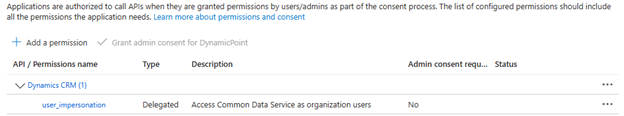
- Click Add Permissions
- The permission doesn’t require an Admin consent.
- At this point the permissions of your application should look like this:
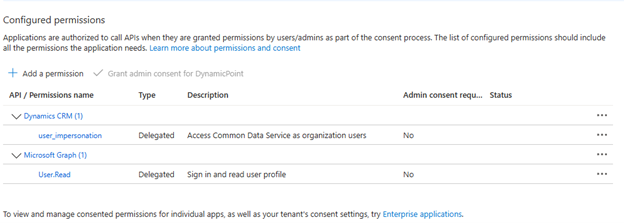
- The next step is to provide security to your app. Go to Certificates and Secrets from the left menu and click New client secret:
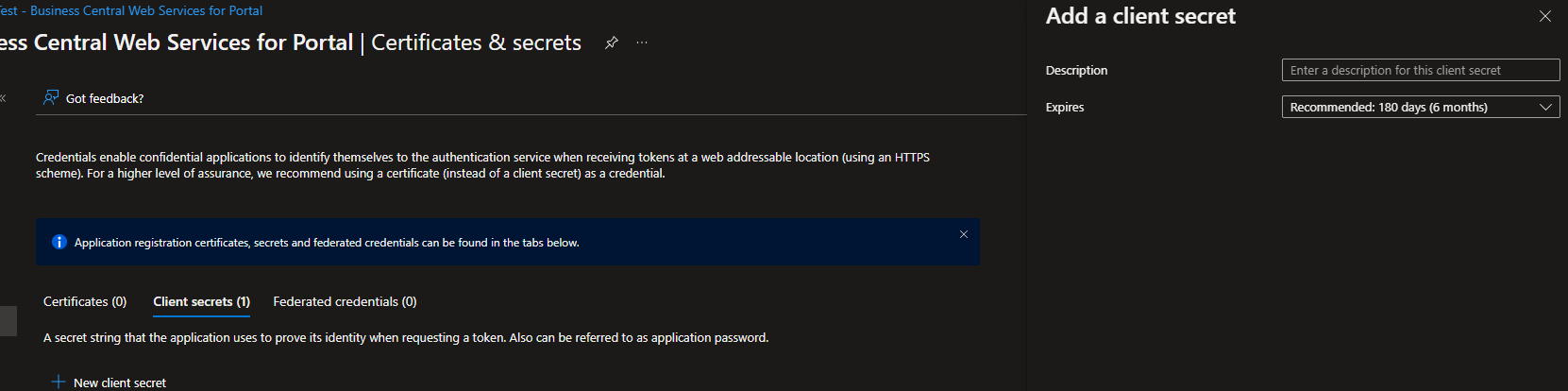
- On the next dialog provide a description of the secret and expiration, then click Add
- Make sure you copy the new secret immediately, as later it will not be available for copying:
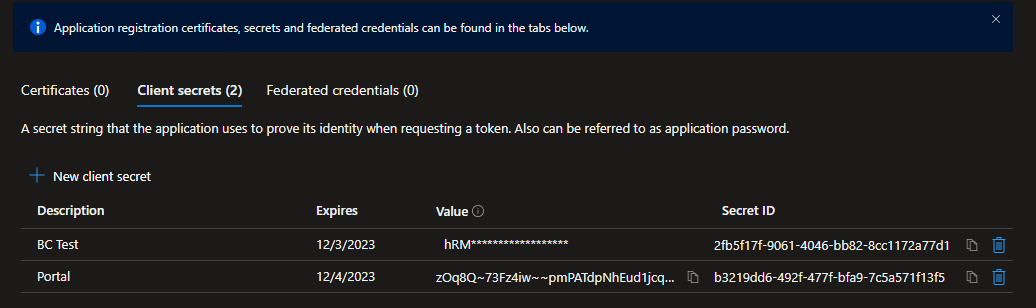
- If you lose the secret, you will need to create a new one and register in the client application.
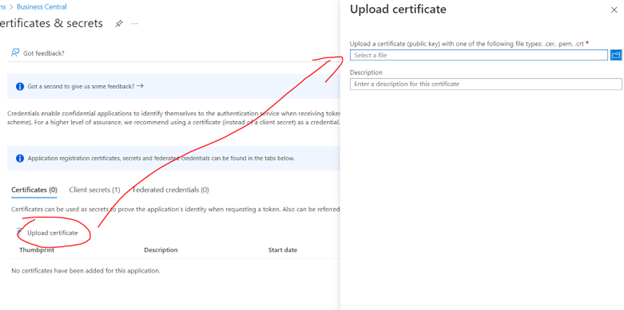
- Alternatively, you can register a certificate to authenticate with the app (you will need the .cer version of the cert here):
3 Power Platform Registration
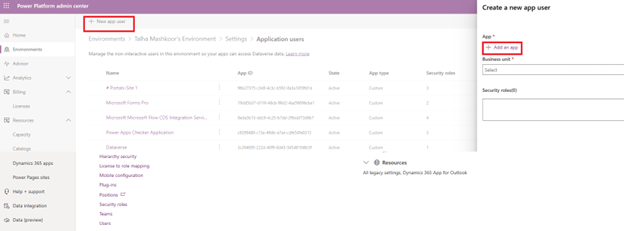
- Log in to Power Platform Admin Center application, click on the target environment and +New App User icon and select Add an app.
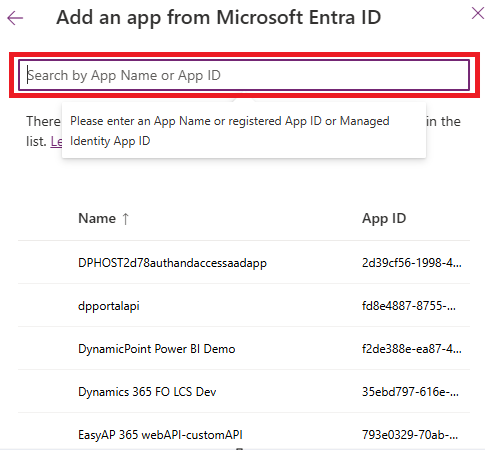
- Click Microsoft Entra Applications from the results. On the new dialog click New
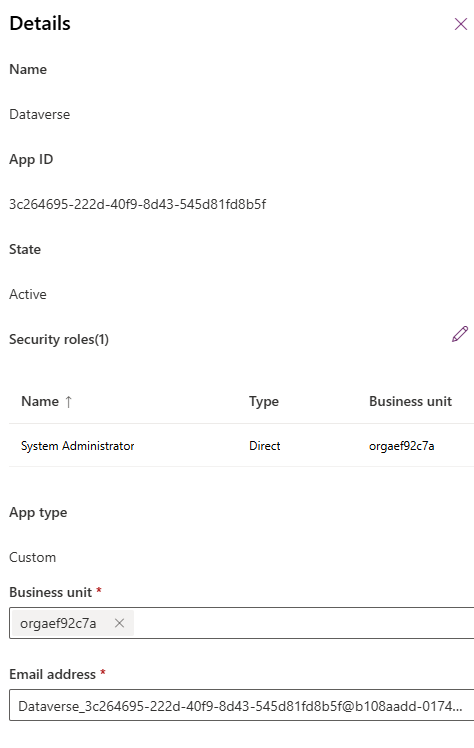
- The Azure Application Card appears, provide roles and APP ID as specified below:
- You need to get the Client ID from the app registration that was just created. Go to Overview from the left menu and copy the Application (Client ID):
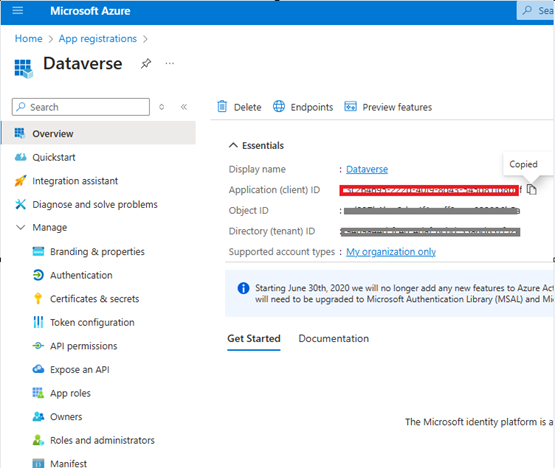
- Paste it into Client ID. Set a Description and change the State to Enabled.
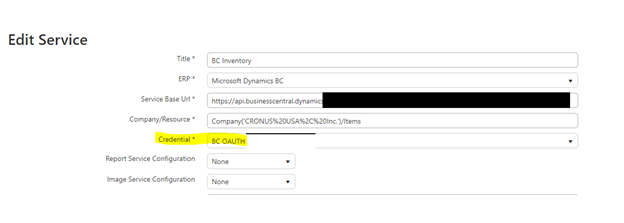
4 Customer / Vendor Portal
In Portal you can configure credentials either directly in the application as custom credentials or you can create predefined credentials in Tenant Admin and pick them in the application. This can be useful in cases when a client uses more than one DynamicPoint product and connects from them to the same Dataverse instance. This section will cover the configuration directly in the application.
- Logon to the application as an administrator
- Click the gear in the upper right corner and select Credentials
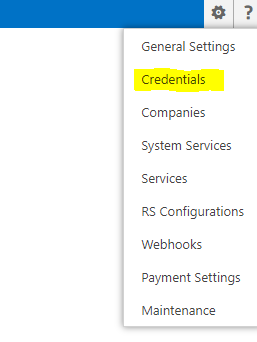
- Click CREATE
- With the Create Credential section, under Credential Type, select Azure AD Application

- Complete the following fields:
– Title
– Credential Type: Azure AD Application
– Credential Configuration: Custom
– Client ID – With the value copied from the registration
– Client Secret – With the value copied from the registration

- Click CREATE to Save New Credential.
- Go into your Portal Services to change the credential to your new OAUTH Credential